In today's data-driven landscape, where organizations generate 181 zettabytes of data by 2025 and face an average data breach cost of $4.88 million, traditional security approaches are failing to protect what matters most: the data itself. This is where Data Security Posture Management (DSPM) emerges as a critical cybersecurity discipline that 75% of organizations plan to implement by mid-2025, making it the fastest-growing security category in the industry.
Understanding Data Security Posture Management (DSPM)
Data Security Posture Management (DSPM) is a cybersecurity technology that identifies sensitive data across multiple cloud environments and services, assessing its vulnerability to security threats and risk of regulatory non-compliance. Unlike traditional security approaches that focus on securing infrastructure or network perimeters, DSPM inverts the protection model by focusing on protecting the data directly, earning it the designation as a "data-first" security approach.
According to Gartner's definition, DSPM provides visibility as to where sensitive data is, who has access to that data, how it has been used, and what the security posture of the data stored or application is. This comprehensive visibility enables security teams to make informed decisions about data protection, compliance, and risk mitigation in increasingly complex multi-cloud environments.
The Evolution from Traditional to Modern Data Security
The shift to DSPM represents a fundamental transformation in how organizations approach data security. Traditional security models were designed for simpler, centralized environments where data resided primarily within on-premises data centers behind well-defined network perimeters. However, cloud adoption has exploded, rendering traditional perimeters obsolete, rapidly increasing data volumes, and giving rise to the phenomenon of "shadow data".
Modern organizations face a complex web of data sprawl, with sensitive data like PII scattered across diverse cloud platforms, SaaS applications, and hybrid environments. In this new reality, it takes just minutes to spin up infrastructure—often without oversight—creating shadow data and environments that frequently go unnoticed unless deliberately discovered.
Core Components and Capabilities of DSPM
DSPM solutions operate through several interconnected components that work together to provide comprehensive data security coverage:
1. Data Discovery and Classification
The foundation of DSPM lies in continuous data discovery and classification of sensitive data across various sources and formats to ensure effective data security management regardless of its location. This includes:
- Automated discovery of structured and unstructured data across cloud, on-premises, and hybrid environments
- Real-time classification using AI and machine learning to identify sensitive data types including PII, PHI, financial records, and intellectual property
- Shadow data detection to uncover forgotten or unmanaged data instances that traditional tools miss
2. Real-Time Monitoring and Risk Assessment
DSPM provides real-time monitoring, vulnerability scanning, and risk assessment of the organization's data security posture to identify and prioritize data security risks and vulnerabilities. This encompasses:
- Continuous monitoring of data access patterns, permissions, and security configurations
- Behavioral analytics to detect anomalous access patterns that could indicate insider threats or compromised credentials
- Risk correlation using AI/ML and integration with threat intelligence to prioritize threats based on actual risk
3. Access Control and Governance
DSPM manages least-privilege access control, ensuring that only the required users can access the data. Key capabilities include:
- Identity and access management integration to analyze who has access to sensitive data and whether it aligns with security policies
- Excessive permissions detection to identify instances where users have more access than needed
- Dynamic permission management that automatically adjusts access based on role changes and security policies
4. Automated Risk Remediation
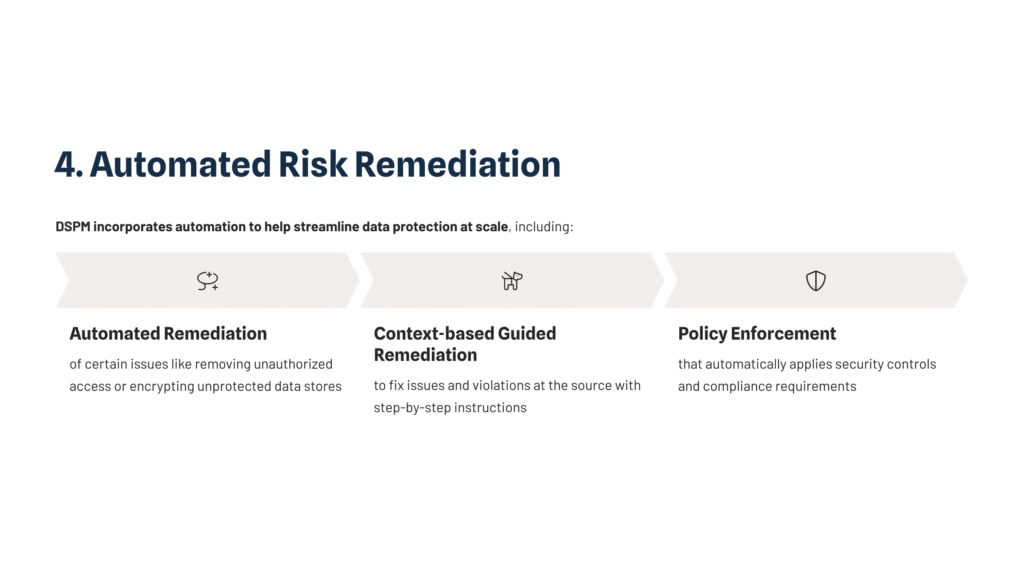
DSPM incorporates automation to help streamline data protection at scale, including:
- Automated remediation of certain issues like removing unauthorized access or encrypting unprotected data stores
- Context-based guided remediation to fix issues and violations at the source with step-by-step instructions
- Policy enforcement that automatically applies security controls and compliance requirements
5. Compliance and Reporting
DSPM solutions provide built-in frameworks to track and attest compliance with GDPR, HIPAA, and more, featuring:
- Automated compliance mapping to over 100 regulatory frameworks
- Real-time compliance monitoring and violation detection
- Audit-ready reporting that demonstrates policy enforcement and risk mitigation
The Critical Challenges CISOs Face Today
Modern CISOs operate in an environment of unprecedented complexity and risk. 71% of CISOs consider themselves more stressed than other C-suite roles within the business, facing challenges that make DSPM not just beneficial, but essential for organizational survival.
The Growing Threat Landscape
83% of organizations have experienced more than one data breach throughout their existence, with insider threats accounting for 20% of data breaches, with the average cost to resolve such threats reaching $15.4 million over a 12-month period. The threat landscape is further complicated by:
- Sophisticated cyberattacks targeting data specifically, with 57% of data breaches in 2022 involving the use of shadow data from unmanaged databases and cloud storage platforms
- Rising regulatory pressures with 2,086 GDPR violation fines totaling EUR 4.48 billion as of March 2024
- The challenge of managing data across multiple cloud providers, with 89% of organizations using a multi-cloud approach
Data Sprawl and Shadow Data Challenges
One of the most pressing challenges CISOs face is the explosion of data sprawl and shadow data. 83% of organizations acknowledge that insufficient visibility into their data weakens their overall security posture. This challenge is compounded by:
- Shadow data creation where 25% of breaches involving shadow data occurred exclusively on premises, highlighting significant unmanaged risks
- Data discovery challenges where only 13% of organizations feel confident that their data classification tools are effective
- Extended breach timelines as breaches involving shadow data took 26.2% longer to detect and 20.2% longer to contain
Compliance and Regulatory Complexity
CISOs must navigate an increasingly complex regulatory landscape where regulatory scrutiny is the primary concern for 70% of respondents who list cybersecurity and data privacy as a disputed risk area. The challenge includes:
- Multiple regulatory frameworks requiring different approaches to data protection
- Strict reporting timelines such as GDPR's requirement to report breaches within 72 hours
- Increasing financial penalties with average GDPR fines now exceeding EUR 2 million
Why DSPM Is Critical for Modern CISOs
1. Addressing the Security Execution Gap
The security execution gap refers to the difference between an organization's data security intentions or policies and their ability to actually execute and implement those policies. DSPM bridges this gap by providing:
- Continuous visibility into data assets across all environments
- Automated policy enforcement that ensures security controls are consistently applied
- Risk-based prioritization that helps CISOs focus limited resources on the highest-impact threats
2. Enabling Proactive Risk Management
Traditional security approaches are reactive, responding to threats after they occur. DSPM enables proactive risk management by:
- Identifying vulnerabilities before they can be exploited
- Providing early warning systems for potential data exposure
- Enabling preventive measures rather than reactive responses
3. Supporting Business Objectives
DSPM doesn't just protect the business—it accelerates it. By providing clear visibility into data risks and enabling faster decision-making, DSPM helps CISOs:
- Align security with business objectives by demonstrating how data protection reduces risk and enables innovation
- Prove value to stakeholders through clear ROI metrics and business impact measurement
- Enable secure digital transformation by providing the foundation for safe cloud adoption and AI initiatives
4. Addressing Modern Compliance Requirements
With over 80% of organizations expressing concerns about the potential leakage of sensitive data during the training and implementation phases of generative AI, DSPM becomes essential for:
- Meeting regulatory requirements across multiple frameworks simultaneously
- Automating compliance reporting to reduce manual effort and ensure accuracy
- Providing audit trails necessary for regulatory examinations and incident response
The Business Case for DSPM Investment
Market Growth and Adoption Trends
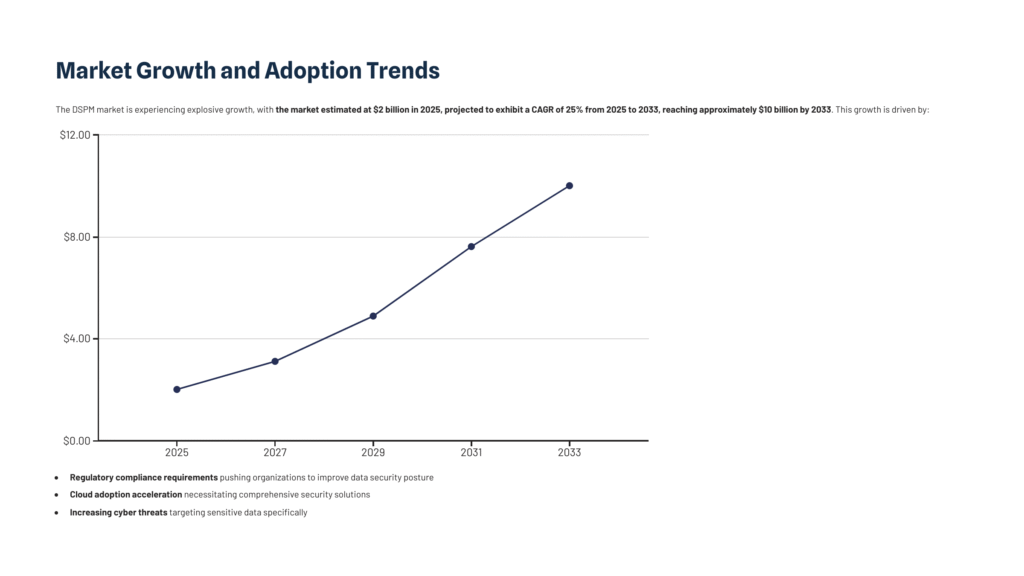
The DSPM market is experiencing explosive growth, with the market estimated at $2 billion in 2025, projected to exhibit a CAGR of 25% from 2025 to 2033, reaching approximately $10 billion by 2033. This growth is driven by:
- Regulatory compliance requirements pushing organizations to improve data security posture
- Cloud adoption acceleration necessitating comprehensive security solutions
- Increasing cyber threats targeting sensitive data specifically
Quantifiable ROI Benefits
Organizations implementing DSPM report significant returns on investment:
- Reduced data exposure risk with quantifiable metrics including cost per exposure and security posture score improvements
- Operational efficiency gains with customers reporting 1,000-2,000 hours saved annually on risk analysis and audit readiness
- Compliance cost reduction through automated policy enforcement and reporting
- Faster incident response with reduced time to detect and contain breaches
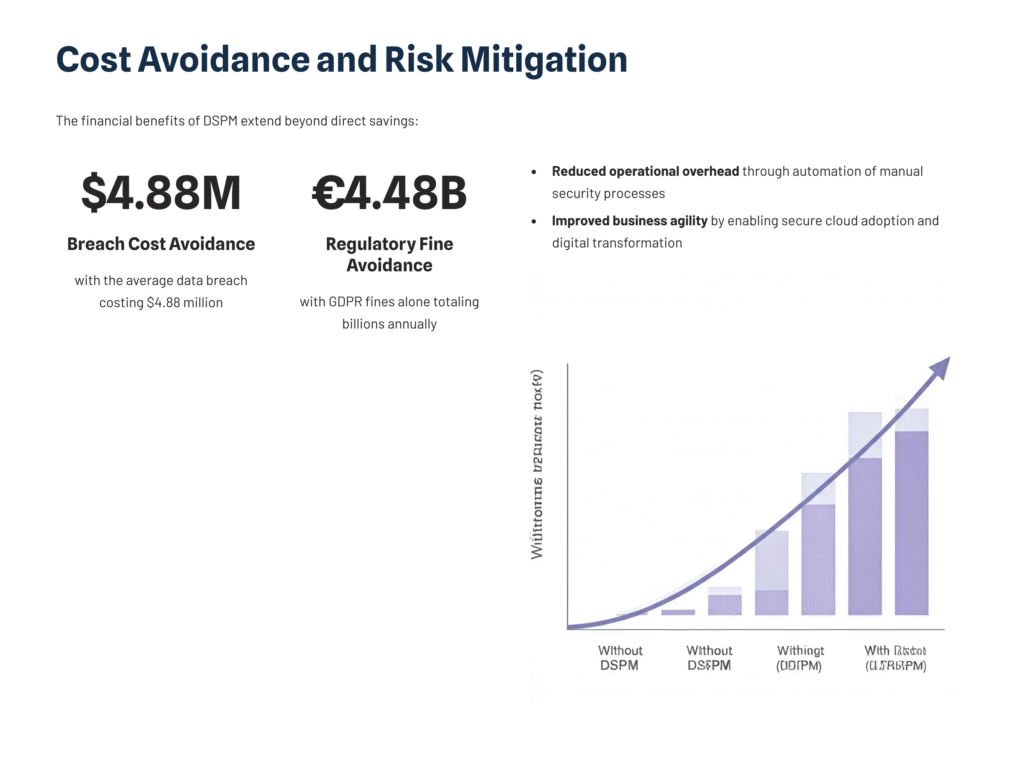
Cost Avoidance and Risk Mitigation
The financial benefits of DSPM extend beyond direct savings:
- Breach cost avoidance with the average data breach costing $4.88 million
- Regulatory fine avoidance with GDPR fines alone totaling billions annually
- Reduced operational overhead through automation of manual security processes
- Improved business agility by enabling secure cloud adoption and digital transformation
DSPM Implementation Best Practices
1. Strategic Planning and Alignment
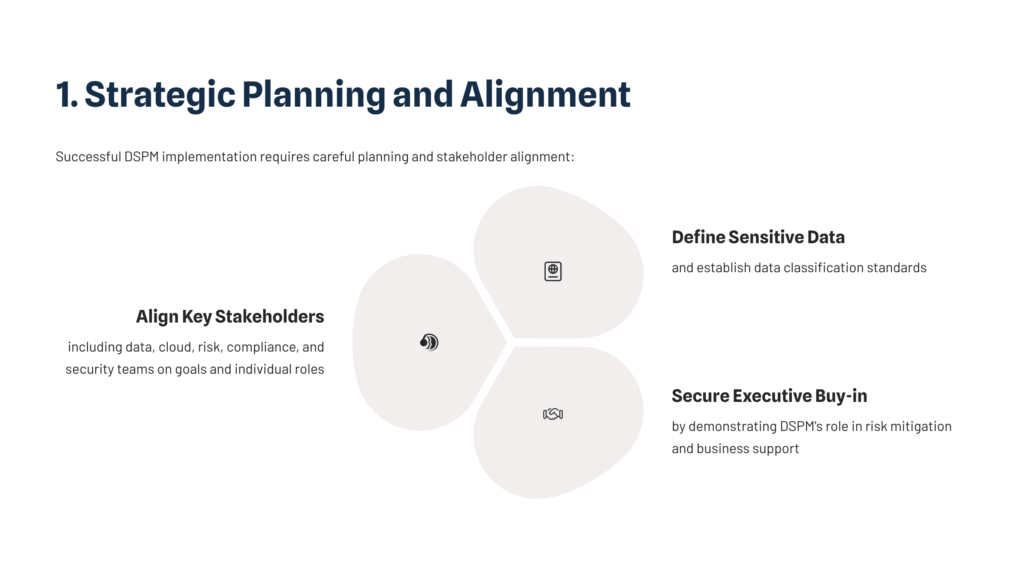
Successful DSPM implementation requires careful planning and stakeholder alignment:
- Align key stakeholders including data, cloud, risk, compliance, and security teams on goals and individual roles
- Clearly define sensitive data and establish data classification standards
- Secure executive buy-in by demonstrating DSPM's role in risk mitigation and business support
2. Phased Implementation Approach

The average DSPM deployment time is 4 to 6 months, with successful implementations following a structured approach:
- Phase 1: Discovery and Assessment (3-6 months for 76% of organizations)
- Phase 2: Policy Development and Configuration
- Phase 3: Integration and Automation
- Phase 4: Continuous Monitoring and Optimization
3. Integration with Existing Security Tools
During initial deployment is the best time to integrate the DSPM with existing security tools. Key integration points include:
- SIEM systems for centralized security monitoring and incident management
- Cloud Security Posture Management (CSPM) for comprehensive cloud security coverage
- Identity and Access Management (IAM) for user authentication and access control
- Data Loss Prevention (DLP) for data protection and movement monitoring
4. Continuous Improvement and Optimization
DSPM is not a one-time implementation but an ongoing process requiring:
- Regular assessment of data security posture and policy effectiveness
- Continuous monitoring of new data sources and changing risk landscapes
- Iterative improvement based on threat intelligence and business requirements
- Regular training for security teams on new capabilities and best practices
The Future of DSPM and Data Security
Emerging Trends and Technologies
The DSPM landscape continues to evolve with several key trends shaping its future:
- AI and Machine Learning Integration for enhanced threat detection and automated remediation
- Zero Trust Architecture alignment for comprehensive data protection
- Generative AI Security to address new risks from AI model training and deployment
- Multi-Cloud and Hybrid Environment Support for comprehensive coverage across diverse infrastructures
Preparing for Future Challenges
CISOs must prepare for evolving challenges including:
- Increased regulatory complexity with new data protection laws and requirements
- Growing data volumes requiring scalable security solutions
- Sophisticated threat actors using AI and automation for attacks
- Business demand for agility requiring security solutions that enable rather than hinder innovation
Conclusion: The CISO Imperative
Data Security Posture Management represents a fundamental shift in how organizations approach data security. For CISOs, DSPM is not just another security tool—it's a strategic imperative that addresses the core challenges of modern cybersecurity while enabling business growth and innovation.
The statistics speak for themselves: 75% of organizations plan to implement DSPM by mid-2025, making it the fastest-growing security category. Those CISOs who embrace DSPM now will be better positioned to protect their organizations, demonstrate value to stakeholders, and enable secure digital transformation.
The question is not whether to implement DSPM, but how quickly and effectively it can be deployed to address the growing challenges of data security in our interconnected, cloud-first world. As data continues to be the lifeblood of modern business, DSPM provides the visibility, control, and automation necessary to protect what matters most while enabling the innovation that drives competitive advantage.
CISOs who recognize DSPM as a strategic investment rather than just a security expense will find themselves better equipped to navigate the complex threat landscape, meet regulatory requirements, and ultimately succeed in their mission to protect their organizations while enabling business success.
Add to follow-up

